What is Event ID 4771: Kerberos Pre-Authentication Failed. Event ID 4771 is a common error message that is generated by the Windows security auditing feature. It typically indicates that a user’s Kerberos pre-authentication attempt has failed.
In this article, we’ll explore the causes and consequences of this error message and discuss best practices for troubleshooting and resolving it.
What is Kerberos Pre-Authentication?
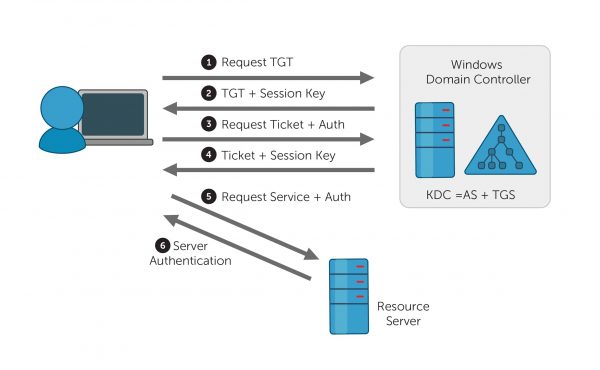
Kerberos is a widely used network authentication protocol in Windows. It provides secure authentication for network resources by using a ticket based system. When a user attempts to access a network resource, Kerberos creates a ticket that contains the user’s authentication information. The user then presents this ticket to the network resource to gain access.
To ensure the security of the authentication process Kerberos uses pre-authentication which is a process of checking user’s credentials before granting them access to a network resource. Windows encrypts the user’s password and sends it to the Kerberos server for validation during pre-authentication. Windows grants user a ticket for accessing network resources, if the password is correct.
What is Event ID 4771?
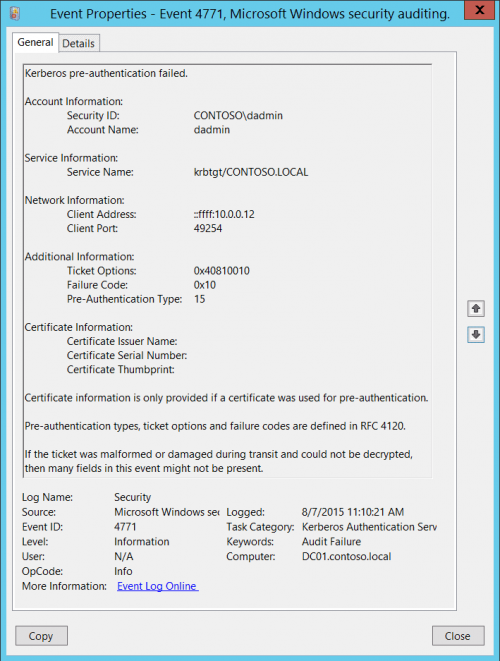
Event ID 4771 is a type of event log message generated by the Windows system’s security auditing feature. This message is logged after a failed user’s Kerberos pre-authentication attempt. The message contains information about the user, the computer, and the reason for the authentication failure.
The message contains:
- Logon Account: The user account used to log on to the computer.
- Source Workstation: Contains the name of the computer from which the user attempted to log on.
- Error Code: Contains the error code that the Kerberos pre-authentication process returned.
The error code provides valuable information about the cause of the authentication failure. Common error codes include:
- 0x18: This error code indicates an account lockout.
- 0x6: The user’s password has expired.
- 0x12: The user’s account is no longer active.
- 0x24: The user’s password is incorrect.
Try our Active Directory & Office 365 Reporting & Auditing Tools
Try us out for Free. 100’s of report templates available. Easily customise your own reports on AD, Azure AD & Office 355.
What Causes Event ID 4771?
There are several reasons why a Kerberos pre-authentication attempt might fail and generate Event ID 4771. The most common causes include:
- Incorrect Password: If a user enters an incorrect password during the pre-authentication process, Kerberos rejects the authentication attempt and generate this Event ID.
- Expired Password: If a user’s password has expired, Kerberos generates this event ID.
- Locked Out Account: If the Windows locks out a user due to too many failed login attempts, Kerberos rejects the authentication attempt and generates Event ID.
- Disabled Account: If Windows disables the account of a user, Kerberos rejects the authentication attempt and generates Event ID 4771.
- Clock Skew: If there is a significant difference in time between the client and the server, Kerberos generates this event ID.
- Malware or Other Security Threats: Sometimes, malware and other other security threats on the network cause this Event ID.
What are the Consequences of Event ID 4771?
Event ID 4771 can have several consequences for users and network administrators. For users, the most immediate consequence is the inability to access network resources. If a user’s Kerberos pre-authentication attempt fails, they are not be granted a ticket to access network resources, even if their password is correct.
For network admins, this event could indicate more dire implications. A large number of such Event ID messages indicate a potential security threat on the network, such as a brute force attack or a malware infection. Additionally, if this Event ID messages are ignored, this could lead to a loss of network security and data breaches.
How to Troubleshoot and Resolve Event ID 4771?
To troubleshoot and resolve Event ID 4771, network admins should follow the following best practices:
- Analyse the Event Log: The first step in troubleshooting this event ID is to analyse the event log message. The error code contained in the message provides valuable information about the cause of the authentication failure.
- Check the User Account: The second step is to check the user account associated with the failed authentication attempt. This may include checking the user’s password status, account status, and lockout status.
- Check the Source Workstation: Network admin should also check the source workstation associated with the failed authentication attempt. This may include checking the computer’s security status and antivirus software.
- Check the Time Synchronization: Time synchronization issues cause clock skew and lead to authentication failures. Therefore check the time synchronization settings on the client and server.
- Check for Malware and Security Threats: If Event ID 4771 messages continue to occur, network admins should check for malware and other security threats on the network.
- Reset Passwords and Unblock Accounts: If the cause of the authentication failure is due to an incorrect password or a locked-out account, network administrators should reset passwords and unblock accounts as needed.
- Implement Multi-Factor Authentication: Multi-factor authentication provides an additional layer of security and prevent brute-force attacks. Network admins should consider implementing multi-factor authentication on the network.
- Monitor the Event Log: Finally, network administrators should monitor the event log for Event ID 4771 messages and take appropriate action as needed: investigating potential security threats and implementing additional security measures.
What is Event ID 4771: Kerberos Pre-Authentication Failed Conclusion
Event ID 4771 is a common error message that is generated by the Windows security auditing feature. It indicates that a user’s Kerberos pre-authentication attempt has failed.
To troubleshoot and resolve it, network administrators should follow best practices that include analysing the event log, checking user accounts and source workstations, checking time synchronization, checking for malware and security threats, resetting passwords and unblocking accounts, implementing multi-factor authentication, and monitoring the event log.
By following these best practices, you can prevent security threats, ensure network security, and provide a secure environment for users to access network resources.