The Importance of Role-Based Access Control in Azure AD. In today’s rapid digital age, it is a must to secure organizational data. One of the key measures to ensure data safety when hosting IT infrastructure in Azure is to adopt Role Based Access Control (RBAC).
Limiting employee access to Azure AD resources to only what is necessary significantly reduces the risk of data breaches and other security incidents. However, implementing RBAC requires creating an Azure environment that adheres to necessary compliances.
In this blog post, we discuss the concept of RBAC in Azure AD, its key concepts, and its importance.
Shall we start with The Importance of Role-Based Access Control in Azure AD?
Azure RBAC vs Role Based Access Control in Azure AD — Differences?
Role-Based Access Control (RBAC) is a feature available in both Azure and Azure Active Directory, but there are some differences between the two.
Azure RBAC is used to manage access to Azure resources, such as virtual machines, storage accounts, and databases.
For example:
Assign the Virtual Machine Contributor role to a user. This allows them to create and manage virtual machines in a specific resource group.
Azure AD RBAC, on the other hand, is used to manage access to Azure AD resources, such as users, groups, and applications and perform specific tasks related to managing Azure AD resources.
For example, you assign the Global Admin role to a user, which allows them to manage all aspects of Azure AD, including users, groups, applications, and policies.
Types of Role-Based Access Control in Azure AD
Built In Roles
Azure AD comes with about 100 built in roles, including roles such as:
- application developer.
- application admin.
- directory reader.
- exchange admin, to name a few.
These predefined roles come in handy when specific role based accessibility permissions need to be granted to users or groups of users.
Please note that roles have a fixed set of permissions and cannot be modified or changed. However, Azure AD includes many roles with varying degrees of access levels, so it’s possible to find the appropriate role for your needs.
By carefully selecting the appropriate roles and access levels to secure your organizational data and ensure that employees have the access they need to perform their roles effectively.
Custom Roles
At times you must create custom roles.
Creating custom roles in Azure AD is a two-step process:
- create the custom role definition, where you define the specific permissions needed for the role.
- create a role assignment to assign the custom role to the user(s).
This is to create highly specific access controls, that fit your organization’s unique needs.
Try our Active Directory & Office 365 Reporting & Auditing Tools
Try us out for Free. 100’s of report templates available. Easily customise your own reports on AD, Azure AD & Office 355.
Key Concepts Of Role-Based Access Control in Azure AD
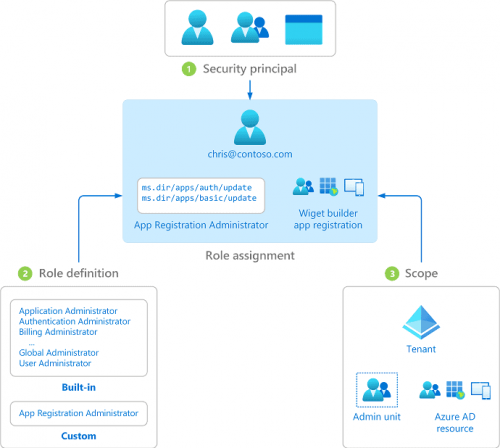
Security Principal
In Azure AD, a security principal refers to the entity that requires access to one or more resources. Security principals take various forms, including:
- Single (users with an Azure subscription).
- Groups of users (should ideally be segregated within Azure AD).
- Service principals (represent applications in Azure AD).
- Managed identities (automatically assigned to applications connecting to resources that support Azure AD authentication).
Scope
A scope is a way to define the specific set of resources or actions that a user or group has access to. The scope of a role assignment determines the level of access that the user or group has to perform specific tasks or operations within that scope.
This approach enhances security, improves manageability, and ensures that users only have access to the resources they require.
Role Definition
After identifying the who and what of the resources to be accessed, the next step is determining how to access them. Define the appropriate set of actions or permissions that a security principal performs, such as read, write, delete, etc. This set of permissions is referred to as a role definition.
Role Assignments
A role assignment is a process of granting a security principal a specific role within a given scope.
By assigning that, you are essentially granting them the permissions necessary to carry out the tasks associated with that role. And the access is revoked as and when required.
To assign a role, an admin must first create a role assignment, which consists of a security principal, a role, and a scope.
Once created, Azure AD RBAC evaluates the role memberships and assignments to determine user access. This ensures that users have the appropriate level of access to resources and helps organizations demonstrate compliance with regulations.
The Importance of Role-Based Access Control in Azure AD
As your company grows the larger workforce, requires advanced ideas and tools. This makes managing data security within the organization a complex task.
To address this challenge, Azure AD RBAC provides a way to maintain data security by restricting access to sensitive resources within the organization.
The following benefits reflect the importance of role based access control in Azure AD:
Improved Security
RBAC allows you to define overarching access controls for Azure AD resources. Create custom roles with specific sets of permissions that determine what actions a user or group performs on a resource.
By limiting access to specific resources, you reduce the risk of unauthorized access and potential security breaches.
Greater Control Over Permissions
With RBAC, you assign roles to users, groups, and managed identities based on their responsibilities, and grant them only the permissions they need to perform their duties. This helps to prevent users from accidentally or intentionally accessing resources they shouldn’t have access to.
Azure AD includes built-in roles, where permissions are only granted to necessary resources. Then, it evaluates role memberships and assignments to determine user access to provide greater control over permissions.
Simplified Management
By enabling RBAC, you simplify the management of access control policies for your Azure AD resources. It eliminates the need to manage permissions at a granular level for individual resources, which are time consuming and error prone.
With RBAC, define custom roles with specific sets of permissions that determine what actions a user or group performs on a resource. This simplifies the process of granting and revoking access, as well as auditing access activity across your Azure AD environment.
In addition, by integrating RBAC with Azure AD, you minimize administrative efforts and provide end-users with a seamless and familiar experience across all integrated applications. This is because Azure AD provides a single sign-on experience for users, allowing them to access all their authorized applications and resources using a single set of credentials.
Enhanced Compliance
Azure AD RBAC provides a framework for controlling access to resources that help organizations achieve compliance with regulatory requirements — local, federal, and state.
Like, it also enables you to generate audit logs that show who has access to which resources, when they’ve been accessed, and what actions they performed.
The Importance of Role-Based Access Control in Azure AD Conclusion
With more organizations moving to the cloud, ensuring data security in Azure AD has become critical.
Why? Because it contains sensitive information about users, such as their passwords, personal information, and access credentials. If this information falls into the wrong hands, it leads to data breaches, identity theft, and financial loss.
RBAC in Azure AD maintains that security but giving access as required. This not only helps to reduce the risk of unauthorized access to sensitive data but also simplifies the management of access control policies at scale.
Try InfraSOS for FREE
Invite your team and explore InfraSOS features for free
- Free 15-Days Trial
- SaaS Reporting & Auditing Solution
- Full Access to All Features